User Roles and Permissions
Last updated 28/05/2024
Introduction to Roles and Permissions
Permissions are grouped together into roles and these roles can be assigned to users in your end-user application. A role contains a set of permissions and identifies the access a user of your application will have.
Permissions give a user the ability to do actions in your application including create, read, update, and delete (CRUD). You grant permissions for each data source in Five and using the CRUD operations will determine the level of access your users will have in your end-user application.
| Permission | Action |
|---|---|
| Create | Adds a new record |
| Read | Selects records that can be read |
| Update | Modifies existing records |
| Delete | Deletes a record |
Granting Permissions
Permissions are granted to data sources, there are three types of data sources in Five:
- Connections
- Queries
- Tables
Permissions can be granted for a group of data sources using the Default Permissions fields on the General page of the Roles form. The permissions granted here will apply to the grouped data sources. For example, permissions set in the Default Query Permissions field will apply to all the queries you have saved in your application for this role.
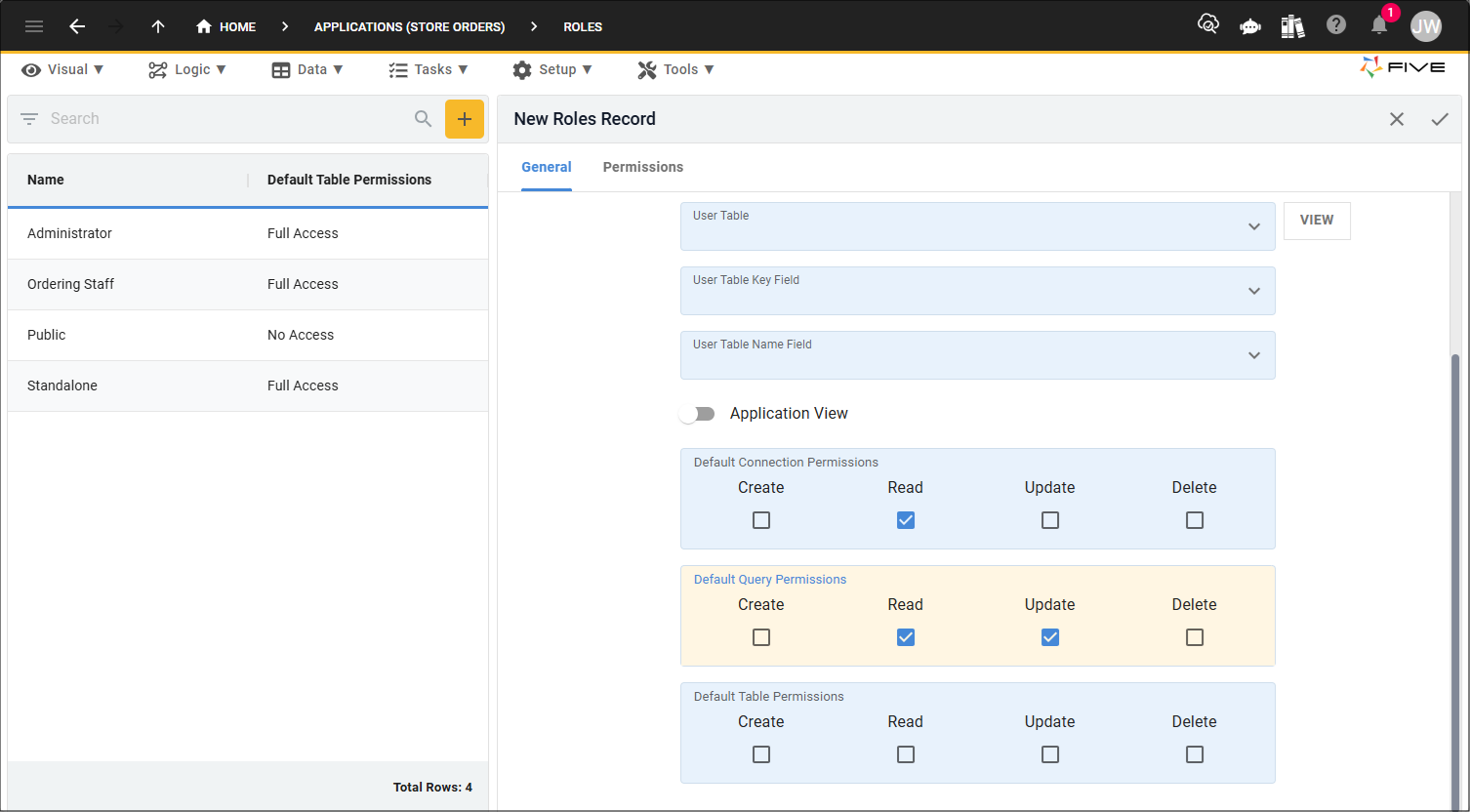
Permissions for each individual data source can be set on the Permissions page on the Roles form. These can be used in conjunction with the default permissions. How this works, is the default permissions will be used for any data sources that have not been individually set, however, if you have granted different permissions to what you have in the default permissions, Five will use the permissions set for the single data source.
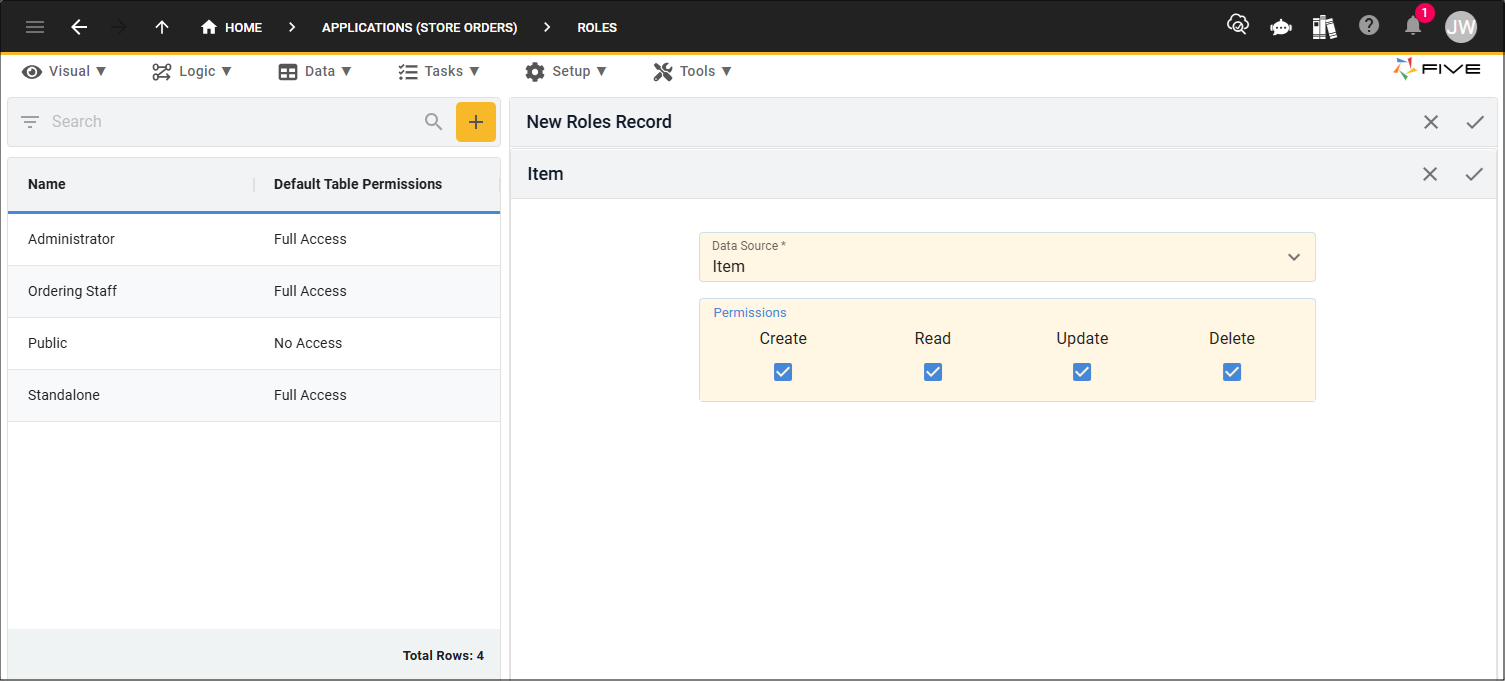
Let's take a look at an example. In the Default Table Permissions field, full permissions are granted for all tables in the Application. These permissions will apply to all the tables in the application.
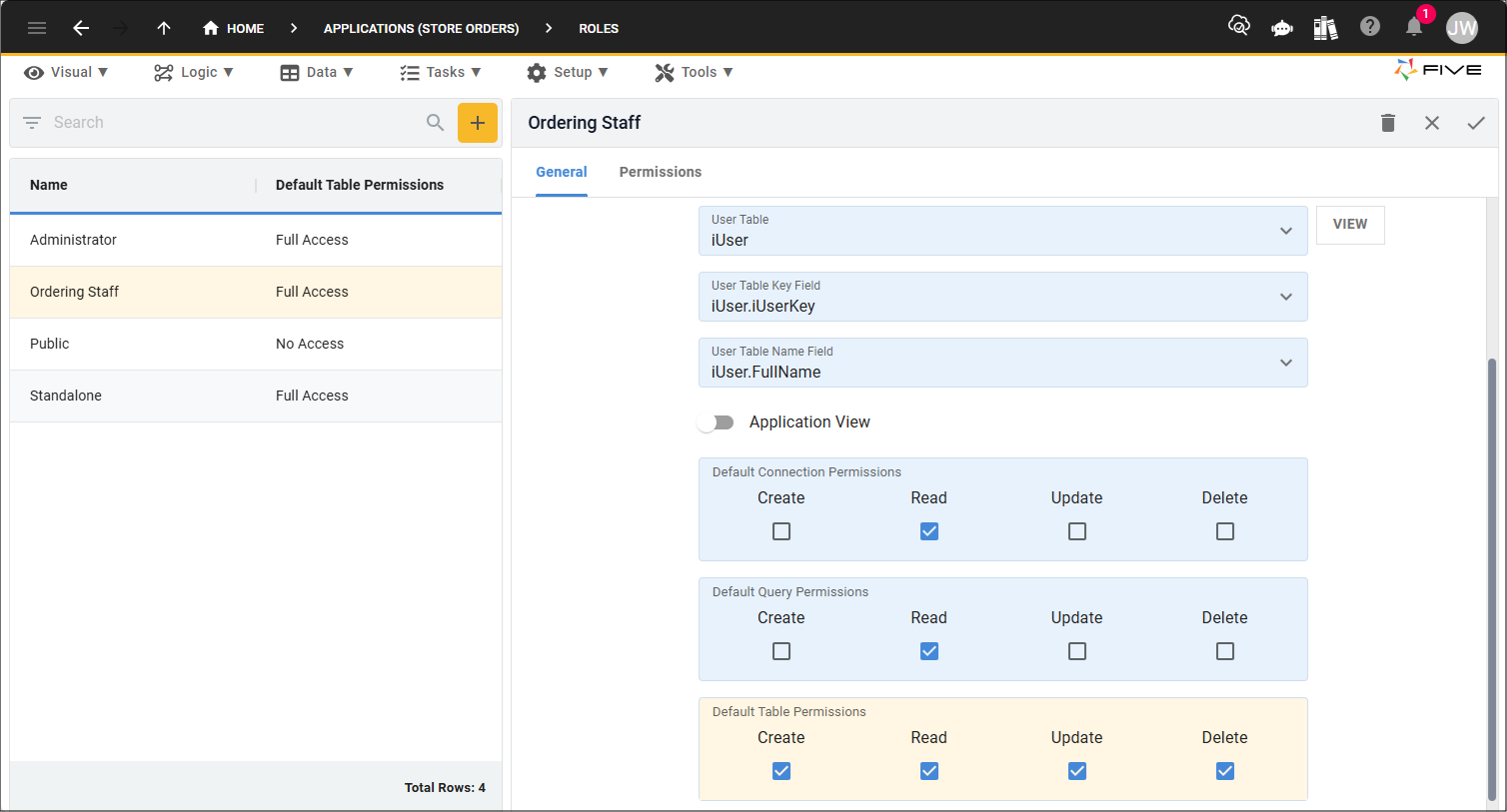
On the Permissions page, the Store data source (table) is selected to only have a read permission. For this role, the Store table will only have read permission applied while the rest of the data sources in the application will still have full permissions.