How Five's Roles Form Works with Your Application's Users Form
Last updated 10/06/2024
The Roles Form
This documentation is to understand the fields on the Roles form in Five and how they work with the Users form in your application. Creating the roles for the users of your application must be done in Five. Assigning these roles to users must be done in your application. All the roles you add for your application will be available in the Role field's lookup on the Users form in your application.
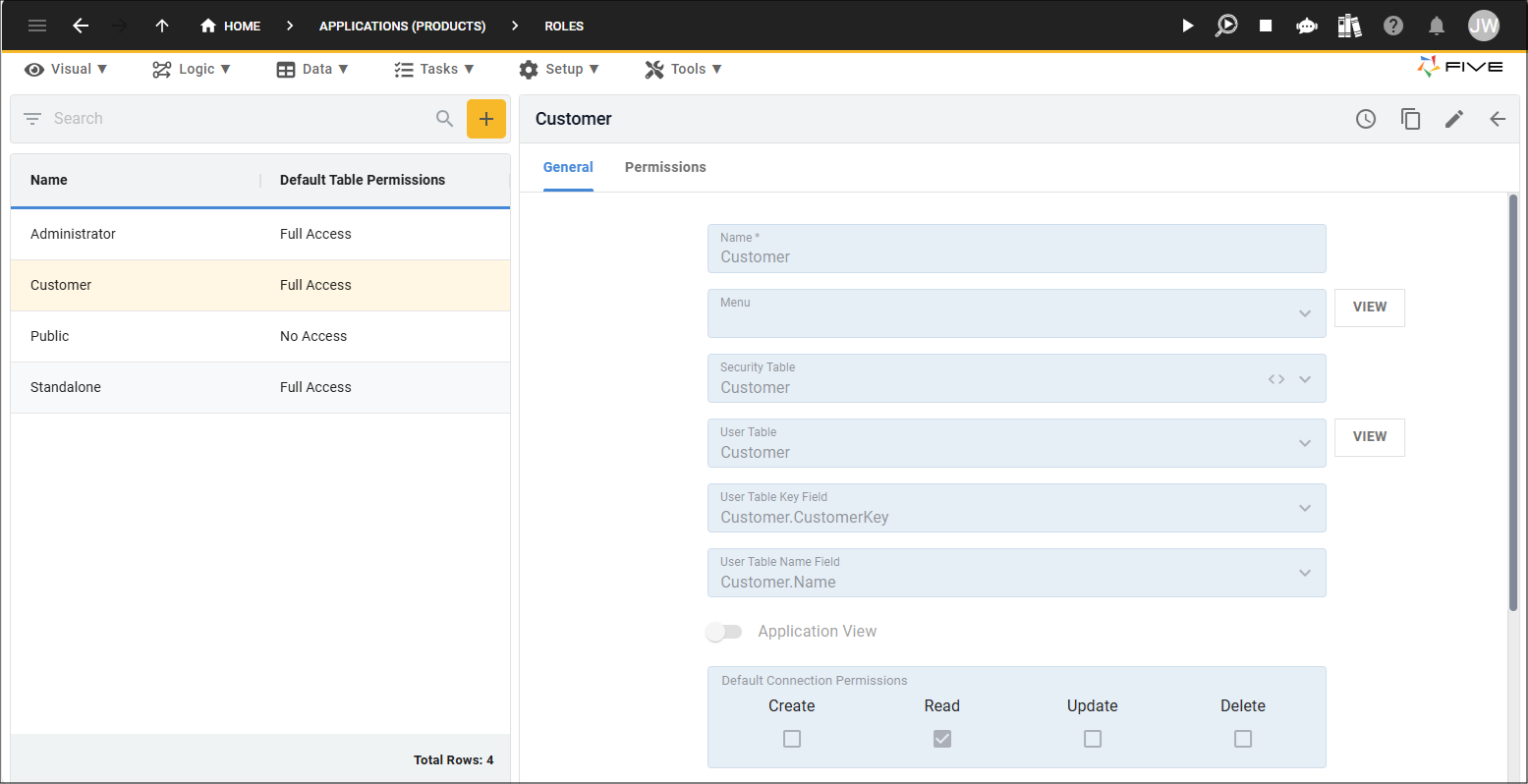
The following table will give a description of each of the fields on the Roles form.
| Field | Description |
|---|---|
| Name | Give your role a name. |
| Menu | Assign a menu for the role, only the menu items in this menu will be displayed to the user with this role. If no menu is specified the user will be structured at the very top of the menu. |
| Security Table | Selecting a table here will enforce Five to filter items that the related user from the user table can view. The user table will need to have a foreign key link to the security table. The only exception to this is if the security table and the user table are the same, then they automatically link via the primary key. |
| User Table | The user table in your application that will be used to map a user from the Five’s user database to a user associated in this table that relates to your application. |
| User Table Key Field | Five will use the supplied key field to map between your application user's database to Fives user’s database. |
| User Table Name Field | Five will use the supplied field for display purposes of the user associated in your application to the user who has logged in via the Five’s authentication which has been mapped between using the User Table Key Field. |
| Application View | If this is checked, this role will be available in the Authentications. |
| Default Connection Permissions | Select the default permissions for all connections in your application for this role. |
| Default Query Permissions | Select the default permissions for all queries in your application for this role. |
| Default Table Permissions | Select the deafult permissions for all tables in your application for this role. |
How Five Maps a User
The user table in your application will be used to map a user from Five's user database to a user associated to the table in the User Table Field field on the Roles form that relates to your application. With the role selected in the Role field on the Users form in your application, Five can dynamically populate the user record list with the entities to the table in the User Table Field in Five.

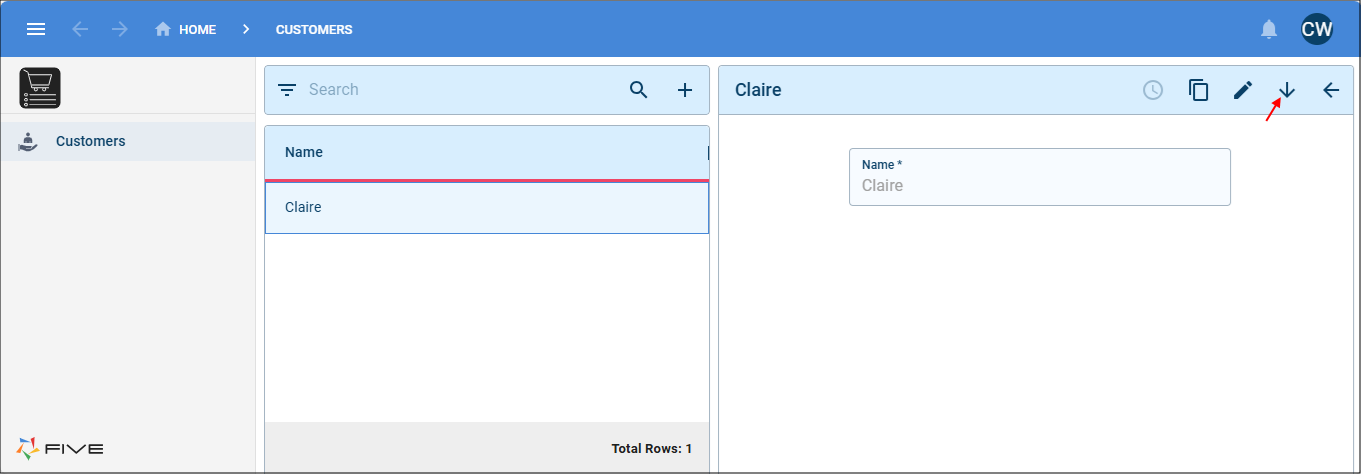
Let's take a look at an example. In an application we have a Customers form that is associated to the Customer table. In Five, the security and the user tables are both using the Customer table, because they are the same table they are automatically linked via the primary key.
When logged in with Five's default admin user, you can see all the customers.
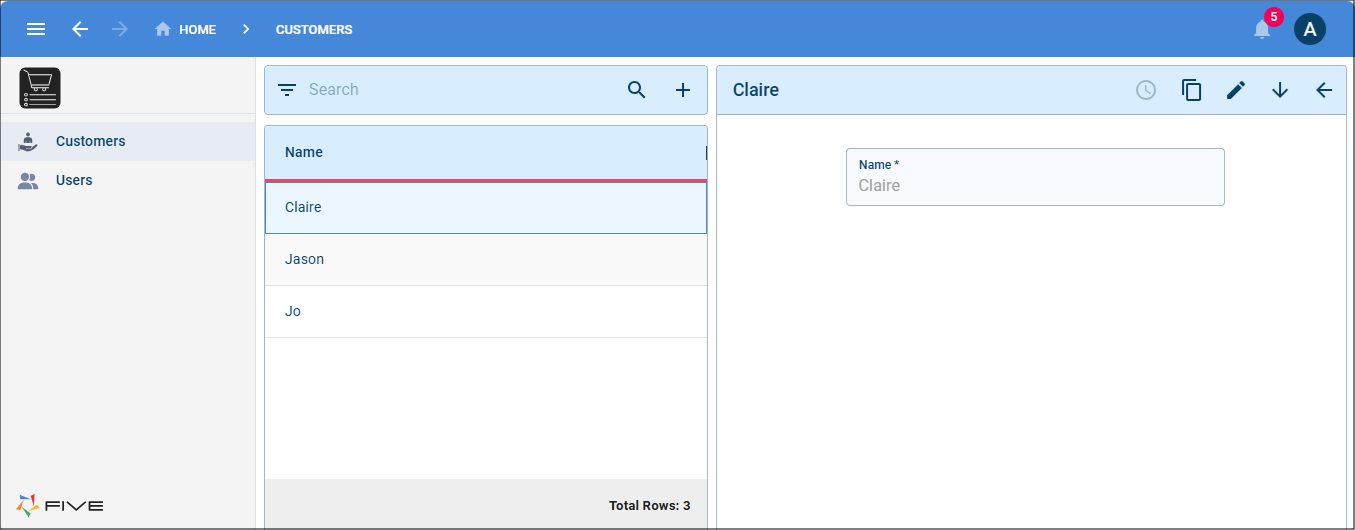
If were to add Claire as a user to the system, once the Customer role has been selected we can add Claire in the User Record field as Five lists all the customers in the system.
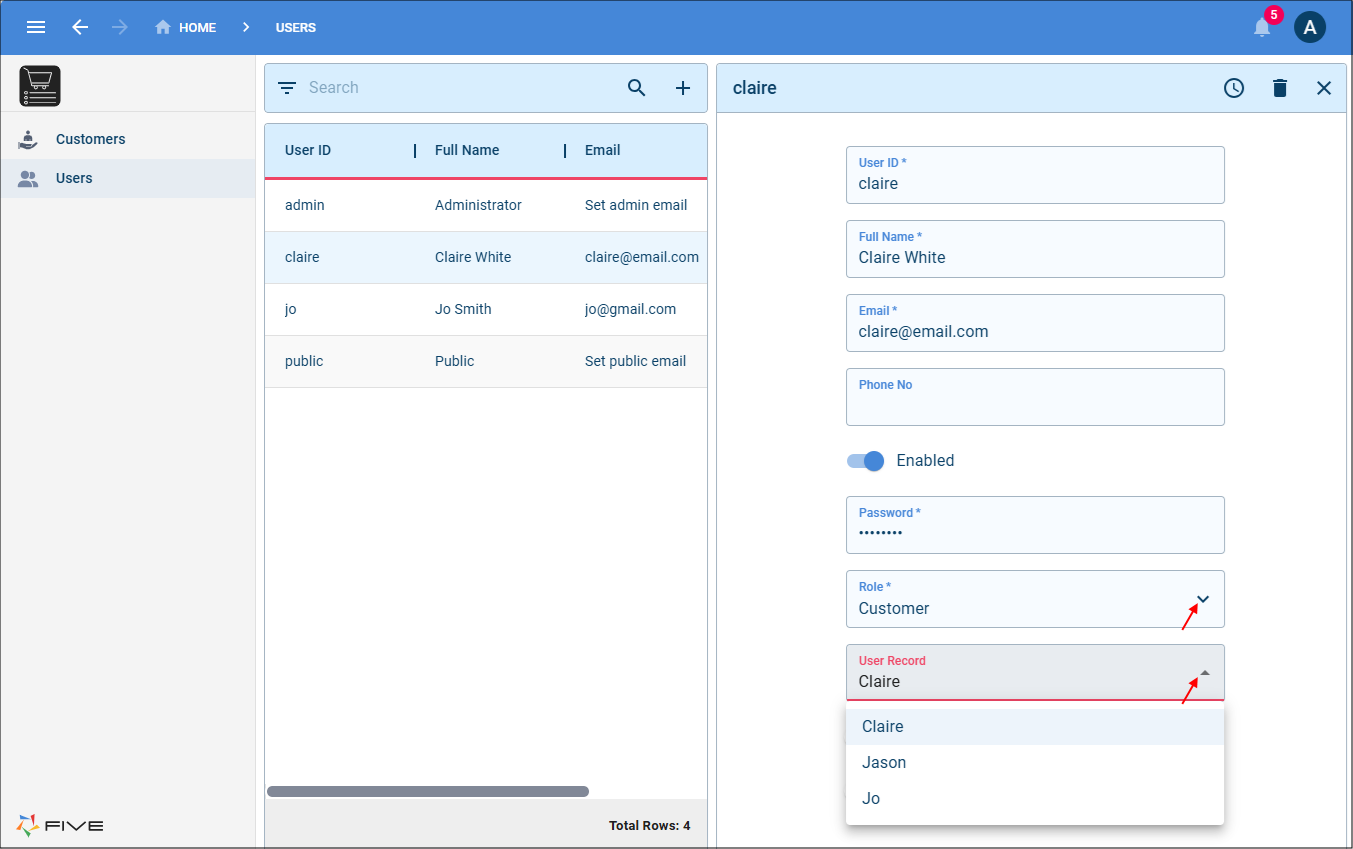
When Claire logs in, she will only see herself as a customer and can drill down and will only see her products.