Introduction
Last updated 5/05/2023
Introduction to Using Authentications
Setup single sign-on for your users to access your applications from anywhere and provide a quick and easy sign-on experience to keep your users productive and reduce time managing passwords. Setting up single sign-on will help ensure that only authorized users have access to your applications and data.Please refer to the following sites for information on OUATH and LDAP.
OUATH
LDAP
Working in the Cloud, you will need the role of Admin or Control to have access to setting up Authentications.
Working with OAUTH
When registering your application with your OAUTH provider, you will need to register a redirection URI for authentication. This will be a combination of your application's URL and the extension sso_login.Examples:
https://admin-default-bookclub-joanne.five.dev/sso_login
https://admin-default-sas-jason.five.dev/sso_login
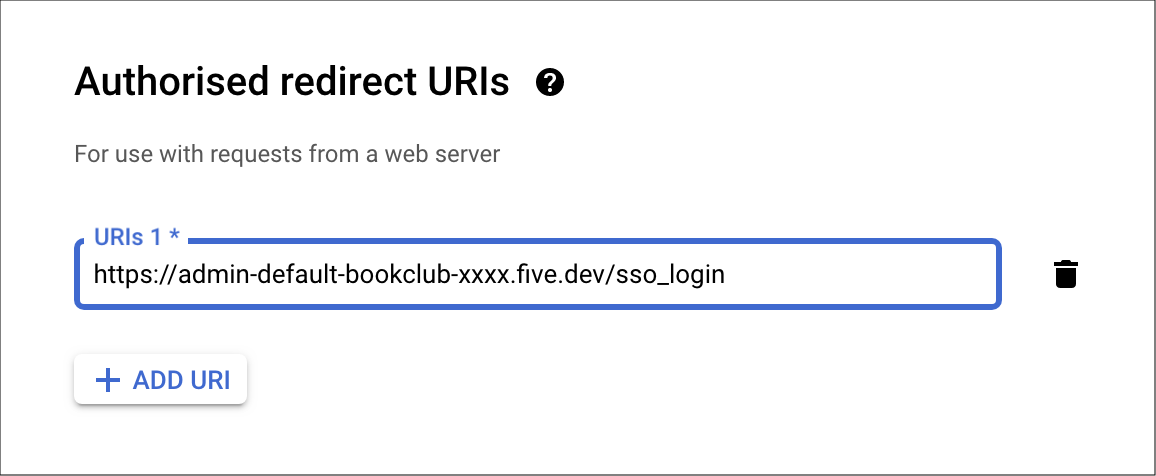
Figure 1 - Redirect URI
Authentications Form
The following documentation gives you an overview of the fields on the Authentications form to help you understand how to set up single sign-on authentication for your applications.| Field | Description | Examples |
|---|---|---|
| Name | The name of the SSO provider. | Google, Active Directory Azure, Facebook, etc… |
| Icon | Provide an icon to show in the optional SSO providers on the Login screen. | |
| Authentication Type | Choose between LDAP or OAUTH. The details for the fields below are catered around SSO via OAUTH version 2.0. | |
| Authentication URL | Provider Endpoint for Authentication from the SSO provider, this should be available on the provider’s web site. | Microsoft Azure (Active Directory) : https://login.microsoftonline.com/{tenant}/oauth2/v2.0/authorize Google : https://accounts.google.com/o/oauth2/auth |
| Token URL | Provider Endpoint to obtain a Token for authorization, available from the providers web site. | Microsoft Azure (Active Directory) : https://login.microsoftonline.com/{tenant}/oauth2/v2.0/token Google : https://oauth2.googleapis.com/token |
| Identity URL | Provider’s Endpoint to retrieving information about the user authenticating via SSO, available from the providers web site. | Microsoft Azure (Active Directory) : https://graph.microsoft.com/oidc/userinfo Google : https://www.googleapis.com/oauth2/v2/userinfo?access_token= |
| Identity Scope | The scope of information about what is required from Five to retrieve about the user authenticating. | Microsoft Azure (Active Directory) : https://graph.microsoft.com/User.Read Google : https://www.googleapis.com/auth/userinfo.email |
| Identity Scope ID | The name of the ID field in the values retrieved about the user. | Microsoft Azure (Active Directory) : sub Google : id |
| Identity Scope Email | The name of the email field in the values retrieved about the user. | Microsoft Azure (Active Directory) : Google : |
| Client ID | The client ID for the registered application with the SSO provider, available from the providers web site. | |
| Client Secret | The client secret for the registered application with the SSO provider, available from the providers web site. | |
| Allow User Creation | If this is set too true, any user authenticated successfully via the SSO authentication process, will be created automatically into the application. | |
| Role | If the Allow User Creation has been set to true, this will be the Role that will be automatically set against the user. |